I previously explained how zero trust’s objectives and principles can prepare you for a ransomware attack. Let’s now talk about actual implementation via microsegmentation.
What Microsegmentation Is, and Isn’t
Microsegmentation is all about breaking your network into segments.
Don’t confuse it with the old network segmentation; we’re not talking about firewalls with rules built around IP addresses. Consider the paradigm shift I noted previously: it’s not all about the local LAN anymore.
Today’s networks are fluid, complex, ever-evolving entities that often incorporate hybrid environments and a wide variety of devices.
Microsegmentation accounts for this evolution by creating what ZScaler refers to as secure zones in which individual workloads are isolated.
Instead of dividing a LAN into segments, microsgmentation centers on partitioning your amorphous network’s zones traffic—server to sever and coast to coast—on a finely granular (micro) level.
Explicit Verification in Action
Recall that one of Zero Trust’s principles is explicit verification. Microsegmentation implements this principle with its identity-based approach.
Whereas network segmentation largely depends on trusting IP addresses (a single point of identification), microsgmentation’s zones are based upon individual workloads. In this context, a workload is a combination of all the process and resources an application needs to execute. Each workload has a unique identity based upon multiple points of data (about the device, user, application, and so on.)
Focusing on workloads instead of addresses is what makes this model so flexible. It is not affected by dynamically changing networks or requirements.
Stopping Ransomware in its Tracks
Let’s apply the first of zero trust’s principles, and assume a ransomware attack will breach your perimeter.
Instead of focusing primarily on north/south traffic (between networks), microsegmentation adapts to east/west traffic (lateral movement, such as between servers). When ransomware slips into one device (say, for example, a VMware server), it must breach wall after wall of security in order to spread. Not only does it have to escape the zone it first slipped into, but it also has to compromise the next zone’s security, then the next zone’s, and so on. See Figure 1.
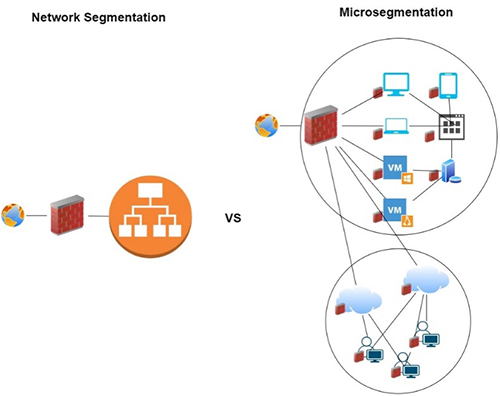
Each time it tries to spread, identity checks are performed at the workload level. This model’s adaptability means It doesn’t matter how the attack slips in—be it via exploiting an on-premise machine’s hardware vulnerability or compromising a cloud platform—because its workload is quickly cut off from communicating with other workloads.
Worth the Investment
It’s important to note that this article has barely scratched the surface of the zero trust model. A deep-dive could easily fill a manual, if not a book. If this successfully sparked your interest in learning more about the model, I’ll count this as a mission accomplished.
Implementation can’t be done overnight, and should be considered a full transformation effort. It’s nonetheless worth the investment, especially considering that 95% of cyber security breaches are due to human error—not security vulnerabilities or exploits. Ninety percent of organizations surveyed by the Enterprise Strategy Group (ESG) are advancing zero trust to ensure any breaches that may one day occur stay contained. ESG’s research further concluded that the model’s segmentation strategy may avert five cyber disasters per year, saving an estimated $20.1 million in downtime. And 87% of advanced users rated their experience with zero trust as “very successful.” In other words, you can trust zero trust.

