Sponsored Post: Nasuni.
Ransomware is everywhere: According to Enterprise Strategy Group (ESG), 73% of organizations have been the victim of a successful ransomware attack that resulted in financial loss, disrupted business operations, or other impacts (see Figure 1) within the past 12 months, and ransomware was involved in 25% of all breaches according to the 2023 Verizon Data Breach Investigations Report.
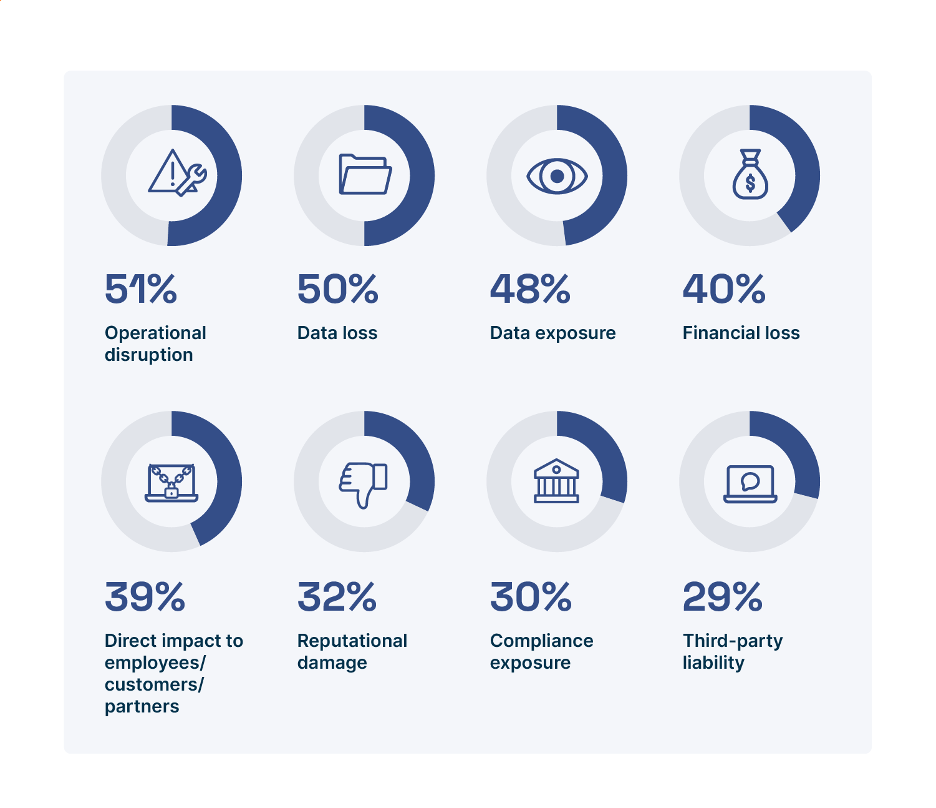
Given the growing and persistent threat of ransomware, it’s more than likely that “It could happen to you” and when it’s your turn to “face off” against ransomware, you don’t want to get caught between “a rock” and a hard place. And when ransomware strikes, seconds count … literally.
Effective ransomware defense requires a comprehensive three-pronged strategy that includes robust protection, detection, and recovery capabilities (see Figure 2).
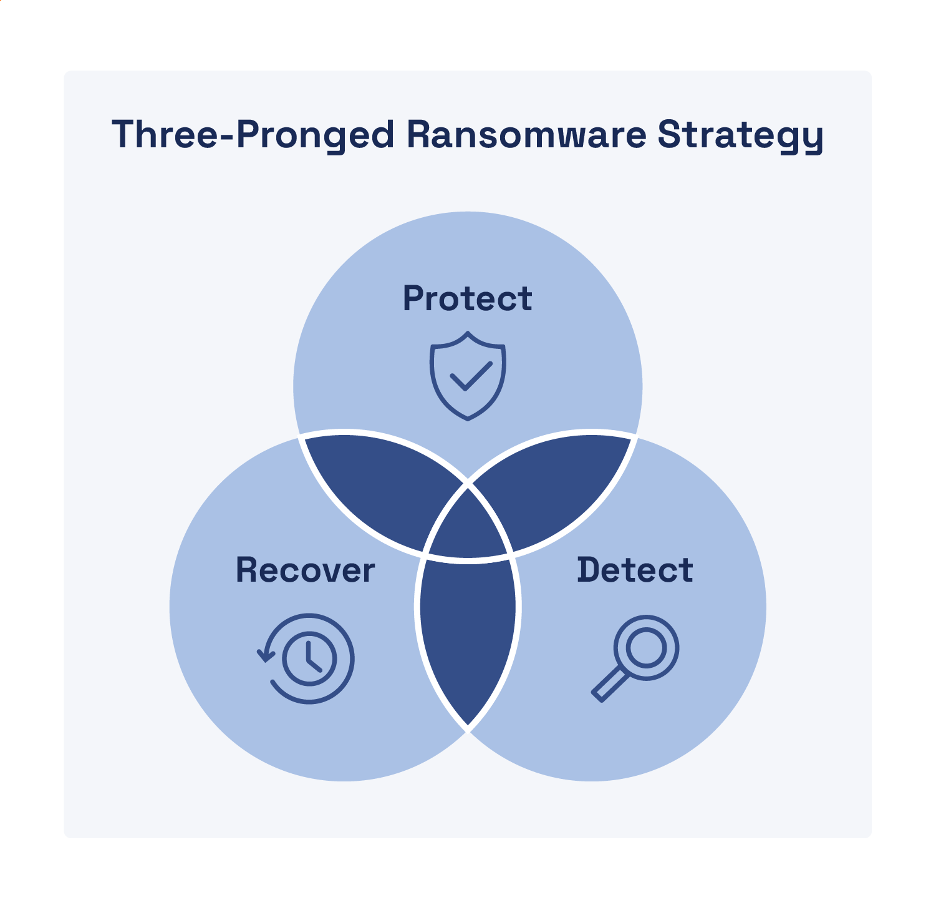
How a Three-Pronged Approach Maximizes Ransomware Protection
Protect
An effective protection strategy focuses on user authentication and limiting access to files and systems based on the principle of least privilege. Your protection strategy should include the following capabilities that also enable containment of ransomware (and other malware) attacks:
- Zero trust authentication (ZTA): ZTA ensures a least-privilege model that enforces continuous verification of authorized users based on the “never trust, always verify” maxim of zero trust.
- Granular segmentation and microsegmentation: Logical segmentation of your network and cloud environments enables targeted containment to restrict lateral movement and block command-and-control (C2) communications.
- Intelligent file indexing: Indexing (and classifying) your data files helps you identify what data needs to be protected and assess the risk and potential impact if your data is compromised.
- Detailed audit logging: Ensure every single operation or permissions change in your environment is logged to help identify potential ransomware (or other malicious) activity.
- Authentication and data access control reviews: Regularly audit user accounts to identify and eliminate dormant accounts and excessive file access permissions.
Rapid containment and eradication are key to recovering from a ransomware attack. If you cannot effectively contain and eradicate a ransomware threat, then recovery is hopeless and even counterproductive—the threat actor can keep encrypting your files over and over. As this vicious cycle repeats, so does the impact to your organization—including financial losses, downtime costs, and reputation damage.
Detect
Detection is important not only to initially identify suspicious or malicious activity, but also to determine when a threat has been effectively contained and eradicated so that recovery can begin. Look for the following capabilities to ensure a robust detection strategy:
- Edge detection: Detect suspicious or malicious file behavior early to prevent ransomware (and other malware) from infecting other file servers, users, and storage repositories.
- Alerting: Leverage artificial intelligence (AI) and machine learning (ML) to accurately and promptly alert incident response teams to anomalous (and potentially) malicious behavior.
- Identifying suspicious file behaviors: Discover potentially malicious activities such as rapid changes to storage repositories, mass file downloads and deletions, and encryption at scale.
Recover
Once containment and eradication are complete, you can rebuild your systems and begin restoring your data—as long as you have secure, reliable, and immutable backups of your data. Unfortunately, restoring millions of files from backup can take weeks or months for most organizations today—during which time business operations may be down or severely disrupted. According to a recent DCIG whitepaper, the average downtime for organizations hit by ransomware was 21 days, and the average recovery cost was $1.85 million—the largest cost associated with ransomware attacks.
Although backups may protect your data, extended recovery operations that take days or weeks will not protect your business. Look for the following capabilities and features in a backup and recovery solution for your organization:
- Rapid ransomware recovery: Recovering millions of files from a ransomware attack should take seconds and minutes—not days and weeks.
- Granular restores: Many snapshot solutions can only recover an entire volume—not specific files or directories—thus users will lose work, even if they weren’t infected.
- Immutable and infinite snapshots: File backups and snapshotsshould be retained long enough to mitigate the risk of ransomware attacks that might take weeks or months to detect.
- Testable/verifiable: Your file data platform should allow you to create a test location to verify the speed and viability of the restore process.
The Best Line of Defense
Nasuni provides the last—and best—line of defense against ransomware with the ability to quickly recover files—which neutralizes the attack—so organizations can minimize data loss and avoid paying a ransom. The Nasuni platform can restore millions of files in less than a minute—because seconds count when it comes to ransomware recovery. Learn more about ransomware threats and how to protect your valuable data from ransomware attacks at nasuni.com and view a demo of Nasuni Rapid Ransomware Recovery.

