Sponsored Post: Nasuni
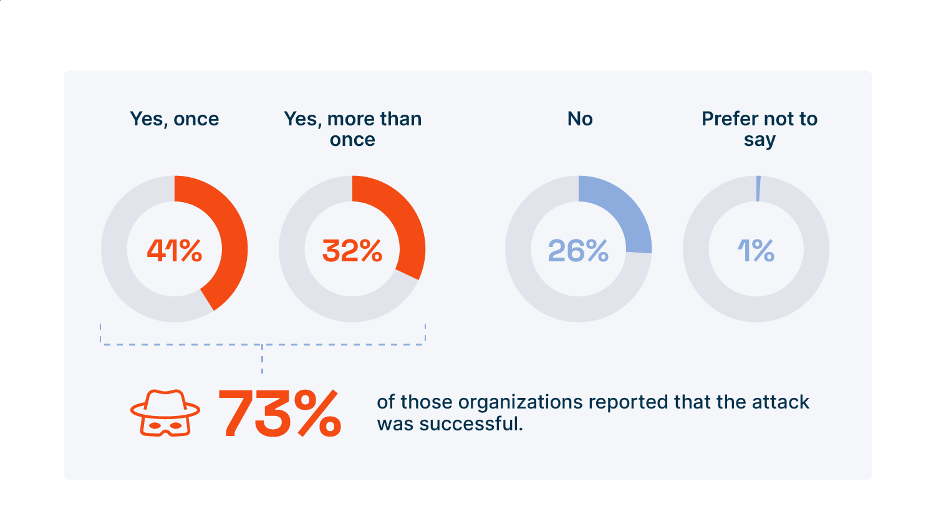
Although many criminals often return to the scene of their crimes for macabre reasons, cybercriminals often return to the scene of a successful ransomware attack for more pragmatic purposes: success breeds success. According to Enterprise Strategy Group (ESG), 73% of organizations have been the victim of a successful ransomware attack, and 32% of those organizations have been the victim of than one successful attack (see Figure 1). For organizations that pay the ransom, it only gets worse: 87% of victims that paid a ransom reported additional extortion attempts by their attackers. Alas, ransomware and its damage to victims—including financial losses, downtime costs, and reputation damage—is not a “one and done” occurrence.
According to the 2022 IBM Security Cost of a Data Breach Report, it took an average of 326 days to detect and contain a ransomware attack and cost an average of $4.54 million (excluding the cost of the ransom itself). Reducing the ransomware attack lifecycle is key to reducing its costs.
Ransomware defense requires a comprehensive three-pronged strategy that includes protection, detection, and recovery (see Figure 2).
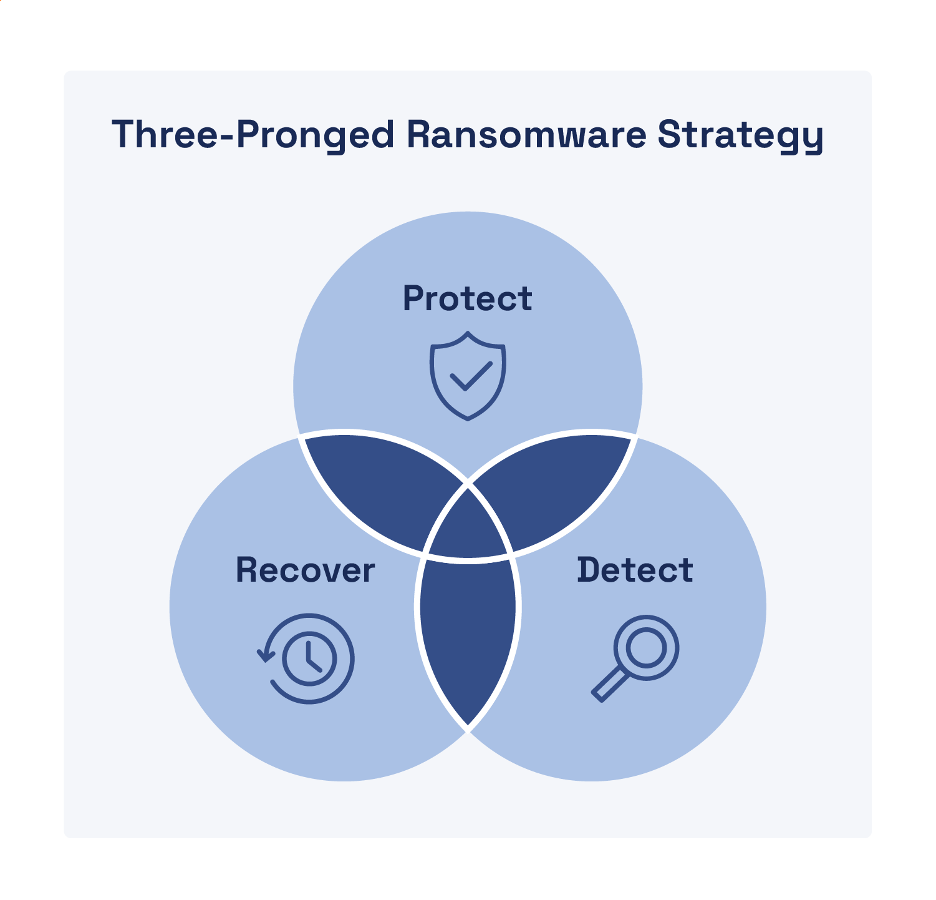
Protection
Most organizations understandably focus their cybersecurity efforts on protecting against ransomware attacks. After all, an ounce of prevention is worth a pound—or perhaps a few million pounds, dollars, or euros—of cure. Your protection strategy should include the following capabilities that also enable effective containment of ransomware (and other malware) attacks:
- Zero trust authentication (ZTA). ZTA ensures a least-privilege model that enforces continuous verification of authorized users before and during file access based on the “never trust, always verify” maxim of zero trust.
- Granular segmentation (including microsegmentation). Logical segmentation of your network and cloud environments enables more targeted containment to restrict lateral movement by attackers, limit damage, and potentially disrupt command-and-control (C2) communications.
- Intelligent file indexing. Indexing (and classifying) your data files helps you identify what data needs to be protected and assess the risk and potential impact if your data is breached, encrypted, and/or exfiltrated by an attacker.
- Detailed audit logging. Ensure every single operation or permissions change in your environment—including opening, moving, modifying, creating, and deleting files—is logged to help identify potential ransomware (or other malicious) activity.
- Authentication and data access control reviews. Regularly audit user accounts to identify and eliminate dormant accounts and excessive file access permissions consistent with the principle of least-privilege.
Detection
Detection of both active and latentattacks, preferably as near to the entry point of the corrupted files/malware—that is “edge detection”—is essential for rapidly containing a ransomware attack and preventing it from spreading unabated throughout your network and cloud environments. Although detection is often thought of in the context of initially identifying suspicious and malicious activity, it is equally important for verifying that containment and eradication efforts are effective and complete. Look for the following capabilities to ensure a robust detection strategy:
- Edge detection. Detect suspicious or malicious file behavior early to help isolate and prevent ransomware (and other malware) from infecting other file servers, users, and storage repositories.
- Alerting. Leverage artificial intelligence (AI) and machine learning (ML) to accurately and promptly alert incident response teams to anomalous (and potentially) malicious behavior by the people and devices accessing your organization’s data.
- Identifying suspicious file behaviors. Rapidly discover potentially malicious activity such as rapid (possibly automated) changes to entire file repositories, mass file downloads, encryption at scale, and unauthorized file deletions.
Recovery
Once containment (and eradication) is complete, recovery can begin—as long as you have an effective recovery strategy that includes ensuring secure, reliable, and immutable backups of your data. Unfortunately, restoring millions of files from backup can take weeks or months for most organizations today—during which time business operations may be down or severely disrupted. To enable rapid recovery of your data—measured in seconds and minutes, rather than days and weeks—you need a file storage and backup solution that includes the following capabilities and features:
- Rapid ransomware recovery. After detecting, containing, and eradicating a ransomware threat, recovering your files should be the shortest operation in your response timeline—measured in seconds and minutes, rather than days and weeks.
- Granular restores. Many snapshot solutions can only recover an entire volume—not specific files or directories—thus users will lose work, even if they were not infected, because the whole volume gets restored from the previous week’s (or worse) snapshot.
- Immutable and infinite snapshots. Newer ransomware attacks can employ a time-bomb effect that might take days, weeks, or months to detect. If file backups and snapshots are not retained for long enough, the risk of losing data and not being able to restore files is greater.
- Testable/verifiable. Your file data platform should allow you to create a test location, either a test directory containing files or a test volume with directories and files, to verify the speed and viability of the restore process.
The Nasuni platform can restore millions of files in less than a minute—because seconds count when it comes to ransomware recovery. Learn more about ransomware threats and how to protect your valuable data from ransomware attacks here.


