Sponsored Post: Nasuni |
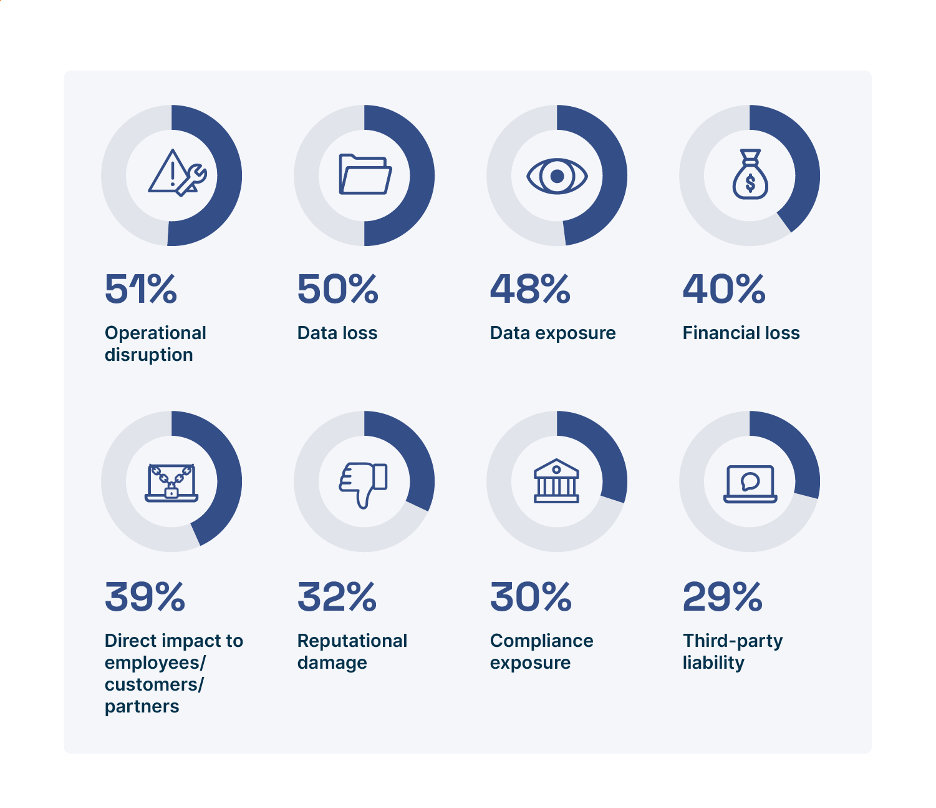
Ransomware attacks have unfortunately become a pervasive and common occurrence for modern organizations. According to Enterprise Strategy Group (ESG), 73% of organizations have been the victim of a successful ransomware attack that resulted in financial loss, disrupted business operations, or other impacts (see Figure 1) within the past 12 months.
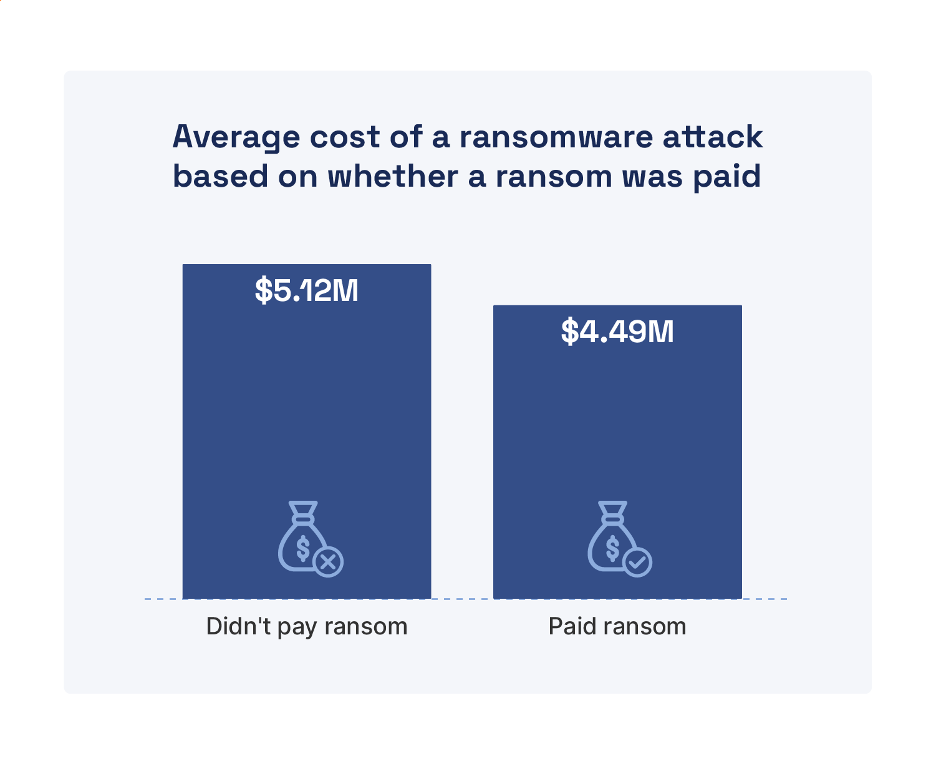
According to the 2022 IBM Security Cost of a Data Breach Report, the average cost of a data breach globally was $4.35 million in 2022, and it took an average of 207 days to identify a breach and another 70 days to contain a breach—a total data breach lifecycle of 277 days. Importantly, the report found that reducing the data breach lifecycle is key to reducing data breach costs—by an average of $1.26 million for a lifecycle shorter than 200 days. Ransomware attacks—not including the cost of the ransom itself—cost an average of $4.54 million and took an average of 49 days longer than other types of attacks to identify and contain. Interestingly, the average cost of a ransomware attack was only slightly less for victims that paid a ransom versus those that did not—not including the cost of the ransom (see Figure 2).
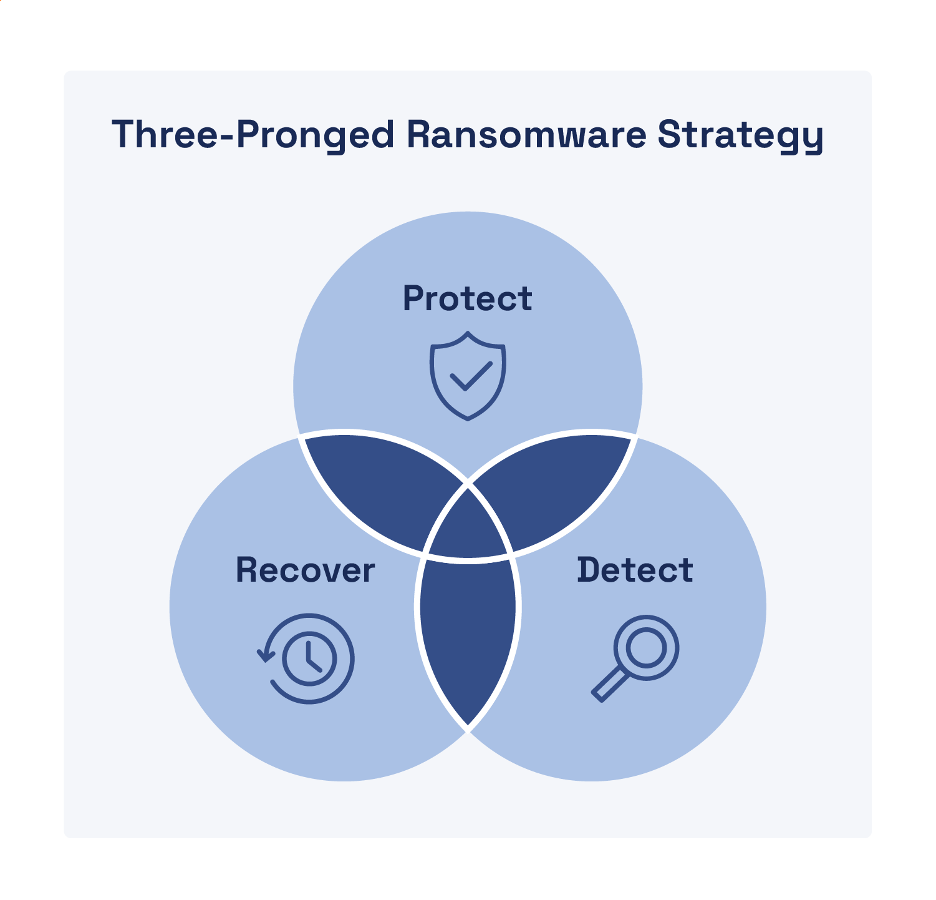
Ransomware defense requires a comprehensive three-pronged strategy that includes protection, detection, and recovery capabilities (see Figure 3). Rapid and effective incident response is critical to recovery from a cyberattack—particularly ransomware, where seconds count. In other types of cyberattacks, threat actors breach a target environment, establish persistence, and move laterally throughout the environment to achieve their attack objectives (such as exfiltrating data), typically over several months.
A ransomware attack follows this same attack lifecycle lasting many months, but when the threat actor ultimately “pulls the pin” to encrypt your data—you have seconds to respond because you are literally racing against the threat actor (and your servers’ processors) to prevent your data from being encrypted. If you are able to block a threat actor’s command-and-control (C2) communications, you can prevent your data from being encrypted. An effective protection strategy from ransomware must include granular segmentation (and microsegmentation) of your environment to enable containment without shutting down your entire network. If you cannot effectively contain and eradicate a ransomware threat, then recovery is hopeless and even counterproductive—the threat actor can just “rinse and repeat” their ransomware attack until you capitulate. As this cycle repeats, so too does the damage to your organization to include financial losses, downtime costs, and reputation damage.
To ensure rapid and effective ransomware recovery, organizations must have incident response plans and ransomware playbooks that:
- Clearly identify key roles and responsibilities
- Document critical decision matrices to enable sound and objective decisions under duress
- Provide step-by-step instructions for containment, eradication, and recovery
Executive leadership and incident response teams must regularly test their plans and playbooks to ensure all team members fully understand what is required of them and can respond effectively.
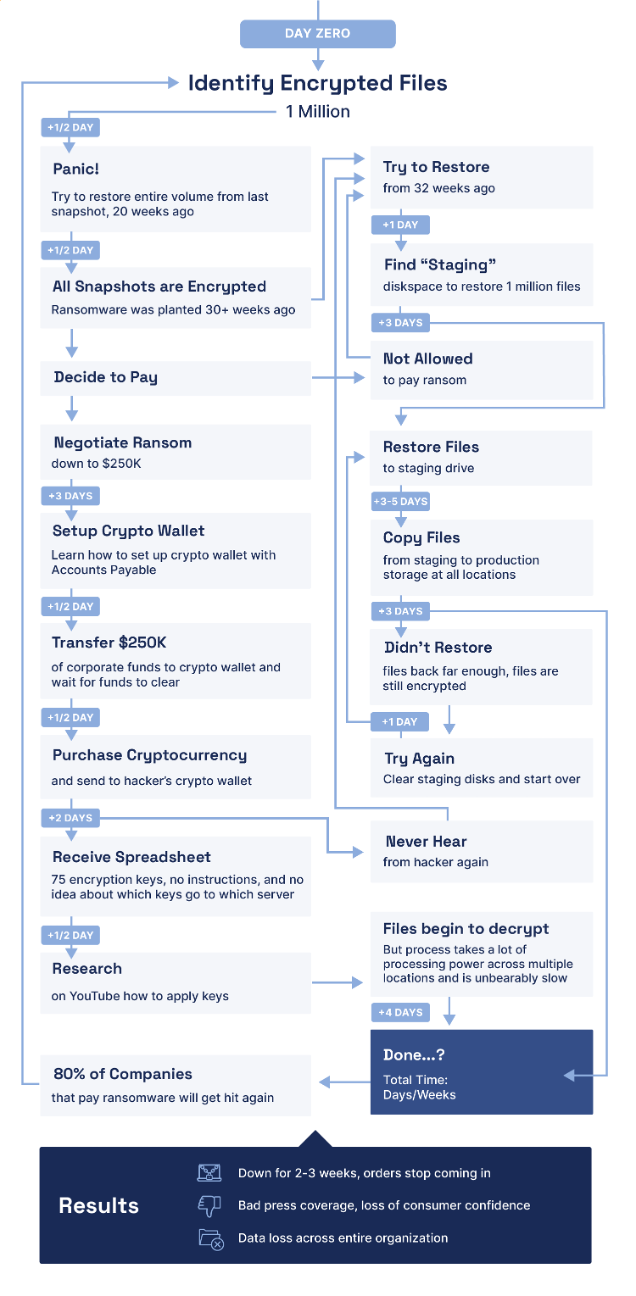
Once containment and eradication are complete, recovery can begin—as long as you have secure, reliable, and immutable backups of your data. Unfortunately, restoring millions of files from backup can take weeks or months for most organizations today—during which time business operations may be down or severely disrupted (see Figure 4).
To enable rapid recovery of your data—measured in seconds and minutes, rather than days and weeks—you need a file storage and backup solution that includes the following capabilities and features:
- Rapid ransomware recovery. After detecting, containing, and eradicating a ransomware threat, your recovery of files should be the shortest operation in your response timeline.
- Granular restores. Many snapshot solutions can only recover an entire volume—not specific files or directories—thus users will lose work, even if they were not infected, because the whole volume gets restored from the previous week’s (or worse) snapshot.
- Immutable snapshots with infinite recovery points. Newer ransomware attacks can employ a time-bomb effect that might take days, weeks, or months to detect. If file backups and snapshots are not retained for long enough, the risk is more significant for losing data and not recovering.
- Testable/verifiable. Your file data platform should allow you to create a test location, either a test directory containing files or a test volume with directories and files, to verify the speed and viability of the restore process.
The Nasuni platform can restore millions of files in less than a minute—because seconds count when it comes to ransomware recovery. Learn more about ransomware threats and how to protect your valuable data from ransomware attacks here.


