Sponsored Post: Larry Miller | Nasuni
MGM Resorts International, which operates more than 30 hotel and casino properties worldwide (including, among others, the Bellagio, Mandalay Bay, and Cosmopolitan in Las Vegas), has recently disclosed that it was the victim of a cyberattack that is suspected to have started on Friday, Sept. 8, 2023, and was first detected two days later Sunday evening.
Unfortunately for the $14 billion industry giant, estimated to bring in more than $13 million per day in revenue on the Vegas Strip alone, this isn’t a fictitious plot hatched by Danny Ocean. Instead, a real-world ransomware heist brought down critical systems and disrupted guest services—including online reservations, hotel registration services, guest key cards, automated teller machines (ATMs), electronic payments, slot machines, elevators, and paid parking, among others.
The attack has been attributed to an affiliate of the Russia-backed Ransomware-as-a-Service (RaaS) gang ALPHV (also known as BlackCat). RaaS allows a threat actor to simply purchase or lease ransomware on the dark web. RaaS customers (or affiliates) can also take advantage of add-on services such as technical support, ransom collection services, and fully outsourced management of a ransomware attack.
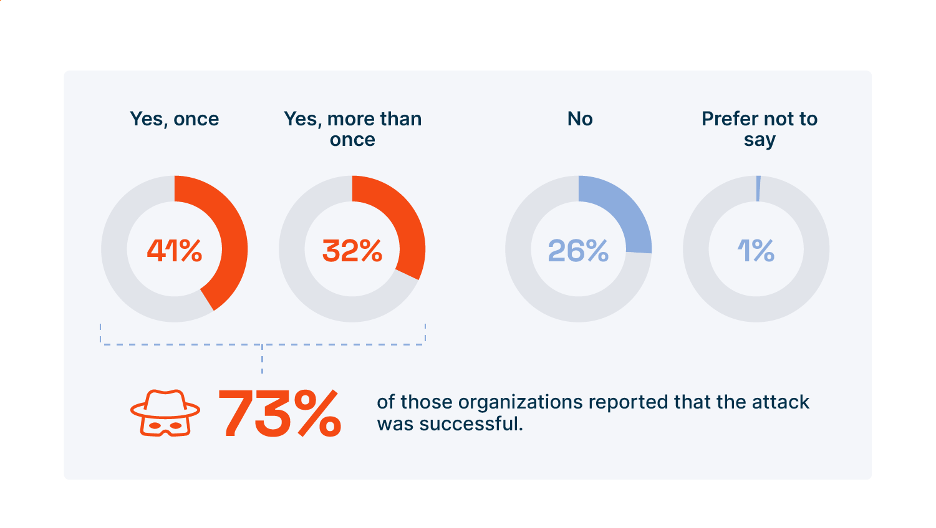
Interestingly, ALPHV also seems to have its own public relations office. In a statement on its leak site, ALPHV decried VX Underground, a cybersecurity firm, for “falsely reporting events that never happened” and oversimplifying the tactics, techniques, and procedures (TTPs) used in the attack. In “set[ting] the record straight”, ALPHV further claims that the initial breach did not involve ransomware. Instead, the threat actor claims it exploited unpatched server vulnerabilities to infiltrate MGM’s network and gain privileged access. ALPHV states the ransomware attack started on September 11, when it seized access to more than 100 ESXi hypervisors, after MGM’s incident response team selectively began shutting down critical systems in an effort to contain the attack—a response that ALPHV characterized as “hasty” and “incompetent” resulting from “inadequate administrative capabilities and weak incident response playbooks.” Regardless of the veracity of ALPHV’s allegations, in the wake of the 2019 MGM data breach in which 10.6 million hotel customers had their personal data stolen and published online, it would seem that they are not entirely wrong—as evidenced by two major successful cyberattacks (albeit different attackers and TTPs) in just four years. Sadly, MGM is not alone in this dubious distinction. According to Enterprise Strategy Group (ESG), 73% of organizations have been the victim of a successful ransomware attack, and 32% of those organizations have been the victim of more than one successful attack (see Figure 1).
An effective ransomware protection strategy can be the difference in the success of your incident response efforts when your organization is under attack and the chips are down. Such a strategy requires a comprehensive three-pronged approach that includes protection, detection, and recovery capabilities (see Figure 2).
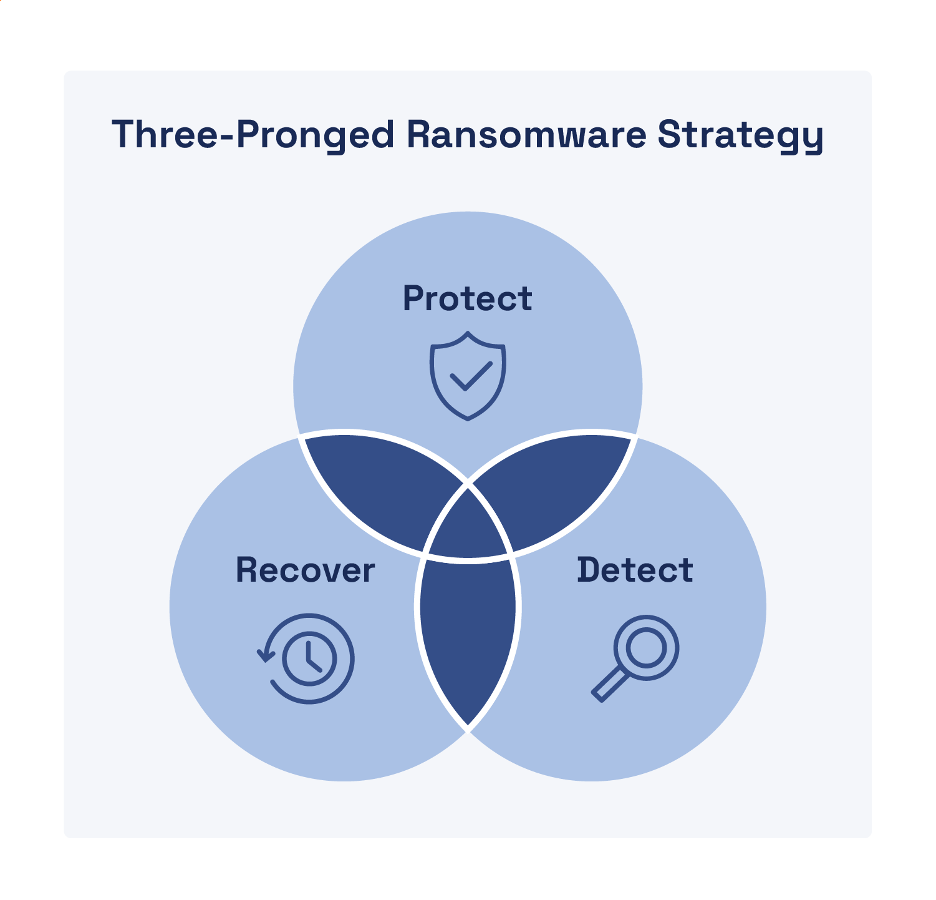
Protection
An effective protection strategy focuses on user authentication and limiting access to files and systems based on the principle of least privilege. Your protection strategy should include the following capabilities that also enable containment of ransomware (and other malware) attacks:
- Zero trust authentication (ZTA). ZTA ensures a least-privilege model that enforces continuous verification of authorized users based on the “never trust, always verify” maxim of zero trust.
- Granular segmentation (including microsegmentation). Logical segmentation of your network and cloud environments enables more targeted containment to restrict lateral movement.
- Intelligent file indexing. Indexing (and classifying) your data files helps you identify what data needs to be protected and assess the risk and potential impact if your data is compromised.
- Detailed audit logging. Ensure every single operation or permissions change in your environment is logged to help identify potential ransomware (or other malicious) activity.
- Authentication and data access control reviews. Regularly audit user accounts to identify and eliminate dormant accounts and excessive file access permissions.
Detection
Detection is important not only to initially identify suspicious or malicious activity, but also to determine when a threat has been effectively contained and eradicated so that recovery can begin. Look for the following capabilities to ensure a robust detection strategy:
- Edge detection. Detect suspicious or malicious file behavior early to prevent ransomware (and other malware) from infecting other file servers, users, and storage repositories.
- Alerting. Leverage artificial intelligence (AI) and machine learning (ML) to accurately and promptly alert incident response teams to anomalous (and potentially) malicious behavior.
- Identifying suspicious file behaviors. Discover potentially malicious activities such as rapid changes to storage repositories, mass file downloads and deletions, and encryption at scale.
Recovery
Once containment (and eradication) is complete, recovery can begin—as long as you have secure, reliable, and immutable data backups with the following capabilities and features:
- Rapid ransomware recovery. Recovering millions of files from a ransomware attack should take seconds and minutes—not days and weeks.
- Granular restores. Many snapshot solutions can only recover an entire volume—not specific files or directories—thus users will lose work, even if they were not infected.
- Immutable and infinite snapshots. File backups and snapshotsshould be retained long enough to mitigate the risk of ransomware attacks that might take weeks or months to detect.
- Testable/verifiable. Your file data platform should allow you to create a test location to verify the speed and viability of the restore process.
Wrapping Up
Don’t play roulette—especially against a Russian ransomware gang—with your valuable customer data. The Nasuni platform can restore millions of files in less than a minute—because seconds count when it comes to ransomware recovery. Learn more about ransomware threats and how to protect your business from costly ransomware attacks at https://nasuni.com.


