Sponsored Post: Dominique Kilman – Director at Unit 42 by – Palo Alto Networks
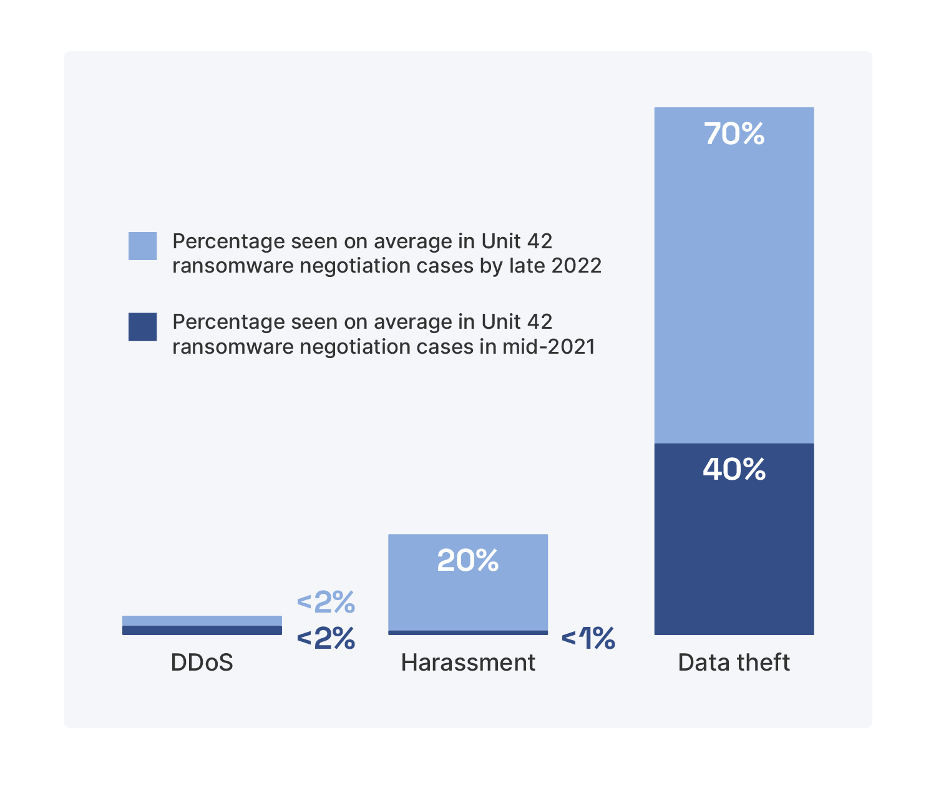
Not surprisingly, ransomware attacks continue to rise as more organizations fall victim to threat actor groups motivated by financial gain, notoriety, and espionage (on behalf of nation-states). However, the nature of ransomware attacks has evolved as multi-extortion attacks—involving encryption (victims pay to regain access to their data), data theft (attackers threaten to release stolen data), distributed denial-of-service (DDoS—public websites and services are shut down), and harassment (attackers directly contact/extort customers, business partners, and media)—have become increasingly common. In fact, approximately 10% of recent ransomware attacks that the Palo Alto Networks Unit 42 responded to on behalf of customers didn’t involve any data encryption. Data theft and harassment, in particular, have risen significantly as preferred extortion tactics over the past year (see Figure 1).
Maintaining reliable, immutable backups is an organization’s best bet for recovering encrypted data without paying a ransom. But attackers are now pivoting to different tactics and techniques to monetize their nefarious efforts. Rather than simply infiltrating a victim’s network, encrypting their data, then demanding a ransom payment, attackers follow an attack lifecycle methodology that includes evading detection, establishing persistence, deploying malware, moving laterally across the network (and connected partner networks), and exfiltrating valuable data. Armed with a copy of the organization’s most sensitive data, an attacker can extort the organization in exchange for not disclosing the stolen data, directly harass and extort customers, partners, and suppliers identified in the stolen data, and/or sell the information on the dark web. This stolen data can also be used by attackers to craft very convincing phishing campaigns against the organization and its customers, partners, and suppliers. The rise of Ransomware as a Service (RaaS) also makes it relatively easy for practically anyone to execute a ransomware attack. RaaS is a subscription-based model that allows threat actors (known as “affiliates”) to use predeveloped ransomware tools to execute ransomware attacks. These affiliates then earn a percentage of each successful ransom payment. In addition to ready-to-deploy ransomware, affiliates can also pay for collection services, technical support, and more. Before RaaS, threat actors needed some proficiency in writing or accessing code to carry out a ransomware attack. With RaaS, threat actors require little-to-no coding expertise.
Beyond backups, organizations must maintain a proactive patch management program to protect against vulnerability exploits that are used by attackers to breach network defenses and infect systems with malware (including ransomware). In 2022, Palo Alto Networks Unit 42 research found a 55% increase in exploitation of vulnerabilities compared to 2021 (see Figure 2).
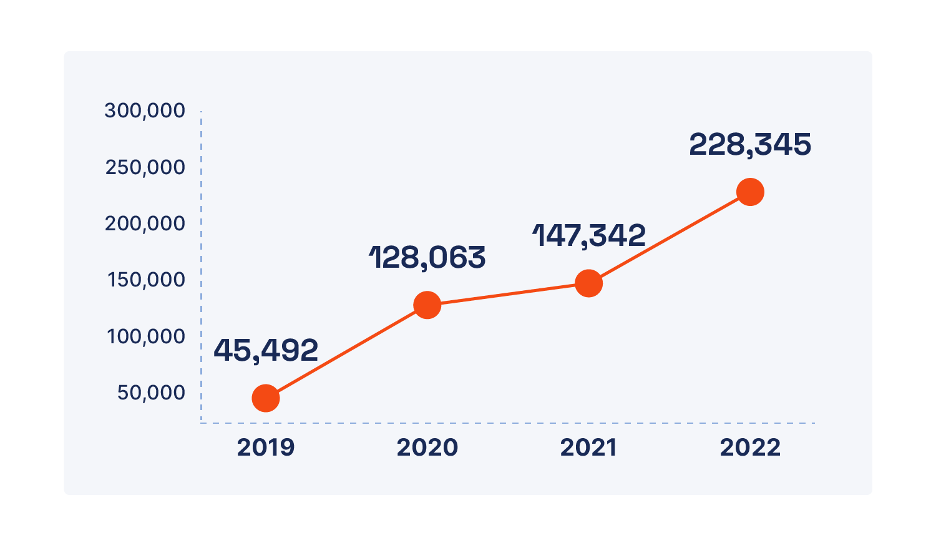
The Log4j and Realtek supply chain vulnerabilities accounted for much of this increase, but other vulnerabilities will inevitably be discovered and exploited in the future. As threat actor groups improve their capabilities, the time between when a vulnerability is publicly disclosed and when it’s exploited continues to shrink. In the case of Log4j, attackers began scanning for vulnerable systems across the Internet within minutes of disclosure.
Phishing continues to be a popular tactic among threat actors for stealing credentials and initially compromising networks. Social engineering is key to a successful phishing campaign, and threat actors will increasingly leverage artificial intelligence (AI), such as ChatGPT, to ensnare even tech-savvy victims. Between November 2022 and April 2023, Palo Alto Networks Unit 42 threat research noted a 910% increase in monthly domain registrations—both benign and malicious—related to ChatGPT, and a 17,818% growth in attempts to mimic ChatGPT through squatting domains (websites that are fraudulently registered to trick victims into clicking a potentially malicious link or visiting a potentially malicious website, for example, https://www[.]pal[.]altonetworks[.]com).
Finally, insider threats are another disturbing trend on the rise. During challenging economic times with a volatile job market, employees may find it tempting to steal valuable information for personal financial gain or, in the case of a disgruntled employee, retribution. With more employees now working remotely at least part of the time in our post-pandemic world, there may be a perception—real or imagined—that no one is watching, and it will thus be easy to “get away with it.”
To protect your organization from ransomware and other threats, a robust security strategy must include the following components:
- A playbook for multi-extortion attacks that includes ransomware negotiation—everything is negotiable, even ransom demands. Retain a professional ransomware negotiator as part of your incident response plan—and “pressure” test your incident response plans regularly to ensure they’re comprehensive and effective.
- Security orchestration and automated response (SOAR) solutions with integrated threat intelligence management and customizable out-of-the-box workflows for automating and speeding response to phishing campaign incidents and mapping of threats discovered in the wild to incidents in your network.
- Proactive attack surface reduction to minimize the number of infection vectors across your enterprise. Be sure to include Linux and mobile devices as the honeymoon is over and threat actors are now targeting these systems and devices as well.
- An effective Zero Trust approach to network access to limit the damage that an attacker can do once inside your network. Microsegmentation with virtual- and container-based next-generation firewalls, continuous verification, and granular access controls restricts lateral movement and enforces the “never trust, always verify” tenet of Zero Trust.
- Take a holistic view of your environment across clouds, datacenters, branch locations, remote and home offices, and mobile devices. Leverage extended detection and response (XDR) technology to rapidly detect and automatically respond to security events as needed.
- Implement robust threat intelligence and vulnerability management programs. Leverage insights from trusted vendors and others in your industry/community to share information and bolster your defenses. Also, remember that not all ransomware threats are associated with “critical” or “high” severity vulnerabilities—in fact, many threats take advantage of the “low-and-slow” medium- to low-severity vulnerabilities that many organizations never get around to patching.
Learn more about ransomware threats and ransomware defense best practices at https://paloaltonetworks.com and hone your Cybersecurity Skills with Cortex here.
Be sure to check out the following resources: