Not only is there a growing rogue’s gallery of ransomware variants, but the tricks they use to strike a victim are growing in variety as well.
Malicious URLs
Tricking a victim to click a malicious URL is the classic phishing method. The trick is simple: Send the victim an email that lures them into clicking a link to a ransomware download.
There are many variations of this tactic, but a particularly nefarious approach is to make the email look like a high priority message from a financial institution, perhaps even threatening to close the user’s account if they don’t click the included link to “verify” their identity.
Such emails can be very convincing via tactics like duplicating real letterheads, logos, and formal language. See Figures 1 and 2. This approach relies on the target panicking and clicking before they have time to reconsider the message’s authenticity.
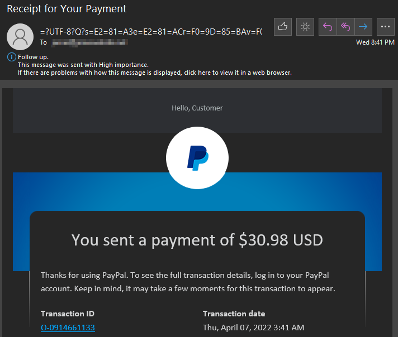
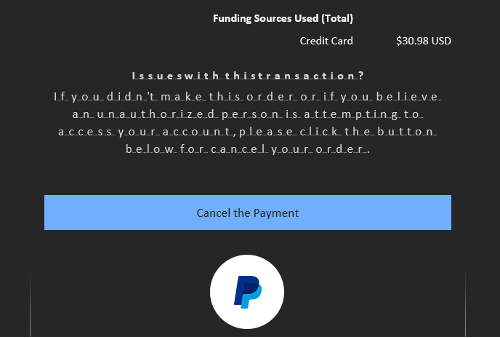
If an email suddenly announces a mysterious transaction, your bank account is locked, or your Amazon account is suspended, take a step back. If in doubt, manually open your browser and type in the URL you always use to login to that account to verify if any such problem exists. Never click the link!
Malvertising
Malicious advertising, a.k.a. malvertising, is an especially insidious vehicle for ransomware delivery. The attacker need only create an advertisement that on the surface appears genuine. If they can manage to get their advertisement included in any typical rotation of ads, it will appear embedded into otherwise safe, trusted sites.
The advertisement hides within it executable code (often JavaScript) that, once clicked, deploys malware—including ransomware—to the viewer’s computer. These are designed to be especially tempting: one popular tactic shows an ad (falsely) warning the reader that their machine is infected, and that clicking said ad will lead them to a security tool to remedy it.
Drive-by Downloads
Drive-by downloads take malvertising to another level, skipping the requirement to click anything. The ad need only appear on a webpage or within an email. Even if you scroll by and ignore it entirely, it will activate its own unseen webpage component that automatically redirects the victim to the attacker’s webpage, which will then try to exploit the browser to begin infection. This method is particularly dangerous because often the victim never knows they’ve been infected until it’s too late.
These downloads don’t always arrive via ads; they can also occur via bundled software. In this scenario, the victim downloads a bundle of legitimate software, wholly unaware that the attacker has snuck their own malware into the bundle beforehand. Simply installing the wanted software can result in launching the attack.
Email Attachments
Delivering malware via email attachments is one of the oldest tricks in the book, and still serves as a useful ransomware delivery method today.
This one is simple to spot and avoid—simply never open email attachments unless it’s from a trusted source and you expected it beforehand. Keep in mind that attackers can pretend to be someone you know, going as far as mimicking (spoofing) their email address.
OS Exploits
Whereas the attack vectors detailed thus far target individuals, attackers have developed more creative methods for infiltrating enterprise networks. Many ransomware attacks today target vulnerabilities within services specific to certain operating systems.
Two of the most popular methods targeting Windows servers involve exploiting Remote Desktop Protocol (RDP) and Active Directory (AD).
RDP attacks target vulnerabilities found within the service. Unlike most types of attacks, this targets an enterprise server first, then once the server is compromised, it spreads to every client that remotes into it, spreading its ransomware payload to all. I’ve written extensively on the topic, beginning with RDP Ransomware: Everything You Need to Know.
AD attacks often aim to steal passwords, exploit services running on AD servers, or compromise AD servers to that they serve to deploy ransomware throughout the enterprise.
Similar approaches are taken when attacking Linux. Linux attackers typically forgo the usual phishing attempts and instead exploit vulnerabilities in either unpatched or misconfigured Linux servers to get their foot in the door. As I’ve written before, most of the world’s web servers run Linux, so ransomware looks to Linux for not only encrypting data but leaking it to the public.
Fake Ransoms
A particularly clever social engineering trick merits an honorable mention, though in this case, no ransomware is deployed nor does any infection ever occur. The attacker will send an email claiming the target has already been infected with ransomware. The email contains no link to click nor any attachment to open, but rather directs the reader to the attacker’s cryptocurrency wallet. Though no ransomware is ever deployed, this attack achieves the same result of ransoming data they claim to have (but do not actually have) for a one-time payment in crypto. An example is shown in Figure 2.
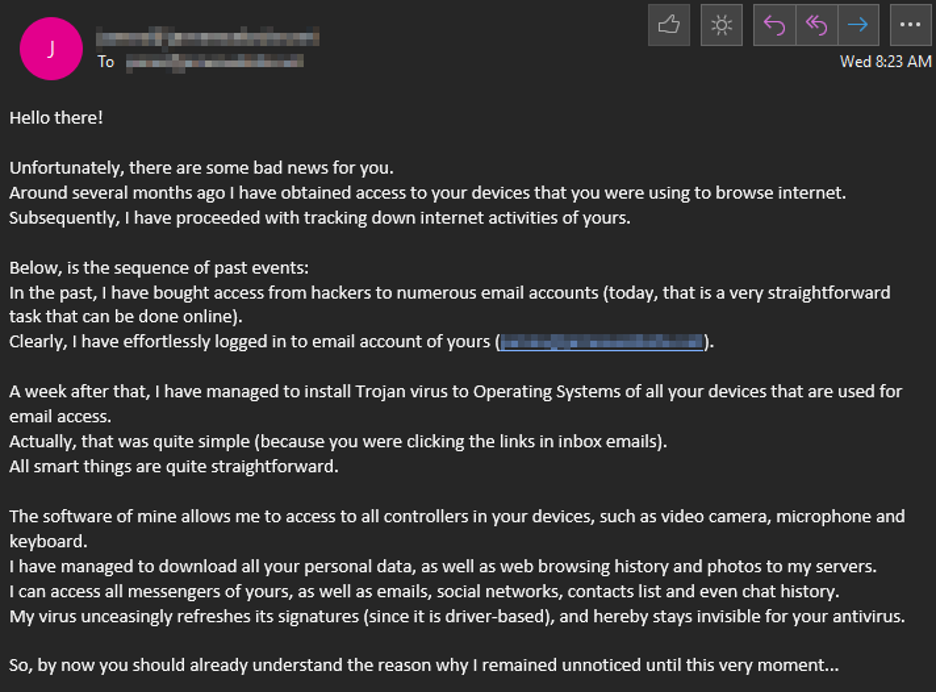
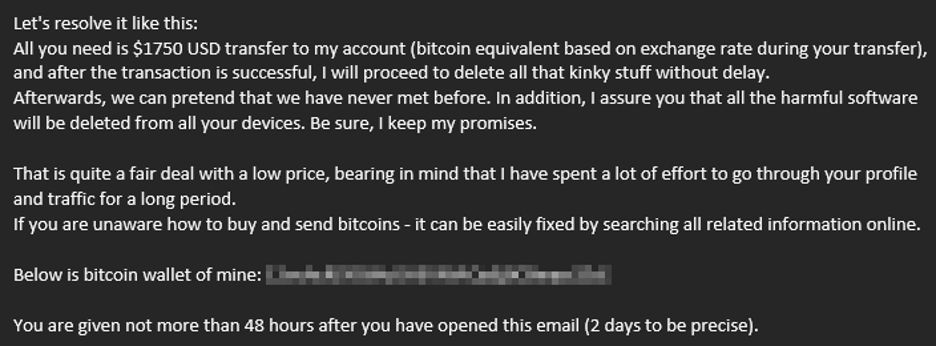
Like Ogres, Effective Ransomware Protection Has Layers
With many different variants of ransomware all taking very different avenues of attack to reach your data, prevention requires multiple layers of defense.
Here are some resources to help get started with that. I recommend beginning with The Top 4 Ways to Prevent Ransomware Attacks, and learning the pillars of recovery: isolate, remove, verify, recover. Stay tuned to ransomware.org for more news and guides on how to identify, prevent, and recover from all varieties of ransomware attacks.

