For several years, defenders and law enforcement have gone to great pains to warn people that ransomware is a global problem. While the organizers of many of the largest cybercriminal ransomware groups are located in Russia, the affiliates of these ransomware groups—the ones who carry out most of the attacks—live in countries around the world.
In 2021, ransomware affiliates were arrested in Ukraine, Romania, South Korea, and Canada among other countries. This is one of the reasons the 30-country ransomware taskforce has been so important in stopping ransomware attacks: It allows for better information sharing and cooperation by law enforcement around the world.
One of the groups that apparently didn’t get the message about ransomware groups being global operations is Conti. In the last 6 months of 2021, Conti was one of the most effective ransomware groups, accounting for 1 in 5 of all “big game hunting” ransomware attacks. When Russia invaded Ukraine, Conti leaders issued full-throated support for Russia.
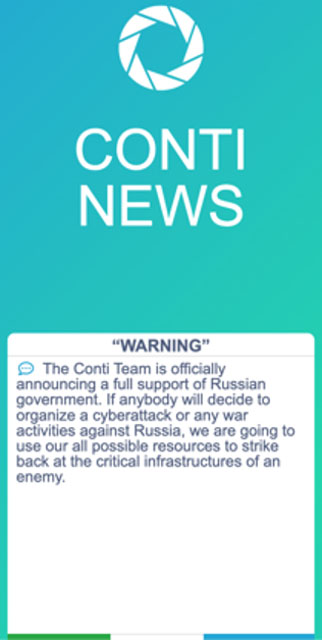
They wrote on their extortion site, “The Conti Team is officially announcing a full support of Russian government. If anyone will decide to organize a cyberattack or any war activities against Russia, we are going to use our all possible resources to strike back at the critical infrastructure of an enemy.”
Several of their affiliates objected strongly to that statement, and one of their “security researchers,” believed to be Ukrainian, decided to punish the Conti leadership by leaking more than a year’s worth of chats, files, and other sensitive information from Conti’s Jabber server and other places.
Several organizations have downloaded, translated and made the leaks searchable for anyone who wants to understand what the day-to-day operations of a large ransomware group looks like.
Here are the 5 biggest takeaways from the leaks.
1. Conti Made a Lot of Money
One of the discoveries made in the leak was Conti’s primary Bitcoin Wallet. According to researchers, since 2017 Conti has received 65,500 in Bitcoin, equivalent to roughly $2.7 billion today. Since the Conti ransomware has only been around since 2019, it is likely a lot of that money came from other activities, but some of that could have come from the Ryuk ransomware which is believed to be operated by the same threat actors.
Either way, $2.7 billion is a great deal of money to collect over a 5-year period, and it shows just how active the threat actors behind Conti have been—not just in ransomware, but in other types of cybercriminal activity.
But they didn’t just make a lot of money, they spent a lot of money as well. During one 13-month period, the leaders of the Conti group spent more than $6 million on salary and bonuses. They also spent significantly on infrastructure and other capabilities during this period, so while they brought in a lot of money, they also had a lot of expenses to cover.
2. A Complex Organizational Structure
This has been known by ransomware researchers for a while, but the leaders of Conti had a complex organizational structure that was constantly fluctuating. Conti’s organizers spent a great deal of time trying to recruit new team members.
Conti payroll was somewhere between 60 and 90 employees, depending on the time of year and the success they had. These are people who worked directly for the Conti organization, and not the ransomware affiliates who operated independently.
According to Brian Krebs, the organizers of Conti hired people who were:
- Coders
- Testers
- Administrators
- Reverse engineers
- Penetration testers/hackers
Coders and testers are responsible for testing and improving Conti’s software, in particular the ransomware executable. This testing went so far as creating fake companies to get meetings with security vendors such as Carbon Black and Sophos to better test their products against Conti’s code.
The administrators are involved in building and tearing down Conti’s command and control infrastructure, extortion site, and other backend servers. These people work with various bulletproof hosting companies to acquire infrastructure and ensure that server bills are paid.
The reverse engineers hunt for vulnerabilities that the ransomware group and its affiliates can exploit. This can be done through finding new vulnerabilities, or figuring out how to exploit known vulnerabilities (which often results in weaponizing published proof-of-concept (PoC) code.)
The penetration testers/hackers use those vulnerabilities, as well as credential reuse and phishing to, gain access to victims, which they then turn over to those who carry out the ransomware attack. The penetration testers are paid per network exploited, which led to a lot of complaints in the chats and on public forums about how bad the pay is, compared to other people employed by the Conti organization.
The team at SecureWorks has done a great job of outlining Conti’s organizational structure in this blog post.
3. Surprisingly Lax Security
There is an old proverb that states, “The cobbler’s children are the worst shod,” which seems to very much apply to the Conti organization. While some members of the Conti team are very skilled at breaking into networks, they were very bad at securing their own infrastructure.
This starts with the Jabber server that they used to carry out much of their communication. They gave everyone who was even tangentially part of the organization access to the server; did not encrypt the chats; and saved all the chat logs.
So, when this breach happened, the attacker was able to access and share almost everything discussed over an almost two-year period. While some members did use an encryption plug-in for Jabber which encrypted those messages, it only accounts for a small fraction of the messages.
In addition to the Jabber chats, the person who leaked the data was also able to pull down logs and chat data from the Rocket Chat server used for technical discussions. These chats contained a lot of information about Conti’s infrastructure, all of which had to be torn down and rebuilt elsewhere.
The Conti members were also very loose in sharing personal information. Several security researchers have been able to use information contained in the chats to find the social media profiles of Conti members.
4. Ties to the Russian Government
It is well-known that ransomware groups based in Russia operate with the tacit approval of the Russian government. But the chats show that the approval may be more than tacit. There are several mentions in the chat of “Liteyny Ave,” which is the location of the Federal Security Service offices in St. Petersburg.
There is also discussion of sources who can assist the group if law enforcement action is ever taken against members. This assistance would appear to come from the Russian government. While the connection is never explicitly made, it is heavily implied repeatedly in the leaked chats. It strengthens the argument that Conti has closer ties to at least some parts of the Russian government than previously believed.
5. Too Close with Some Ransomware Negotiators?
Like it or not, ransomware negotiators have to maintain a cordial relationship with ransomware groups. As useful as it may seem in the short term, being adversarial is only going to be a disservice to their clients.
However, some negotiators seemed to have gotten too chummy with the ransomware group. There are discussions that show negotiators willing to offer insider information, and asking the Conti team to recommend them to new victims.
Most ransomware negotiators do not engage in this type of behavior, but the few that do could give the negotiation industry a bad name. Ransomware negotiators play an important role in helping ransomware victims recover, but it is important to ensure that negotiators are only working on behalf of the victims.
Don’t Let Your Guard Down
There is a lot of valuable information that has been pulled from the Conti leaks. Law enforcement will be using the Bitcoin addresses and other data to issue more indictments and make more arrests, while security researchers will be using the information to develop better defenses against ransomware.
While the Conti leaks are great news, they have not completely silenced Conti. Attacks by the Conti ransomware group have slowed down, but they have not stopped. It is important that your organization still take the necessary steps to protect yourself from Conti and other ransomware groups.

